How I made privacy more accessible
Overcoming syncing barriers in the Iron Fish mobile app
As the sole Designer and Lead, I drove the entire design process—from initial research and persona development to competitive analysis, wireframes, prototypes, and the final mobile app design.
ABOUT THE COMPANY
Iron Fish is a privacy-focused blockchain that encrypts every transaction, ensuring you stay in control of your digital assets. It delivers secure, compliant privacy in an often vulnerable financial landscape.
PROJECT GOALS
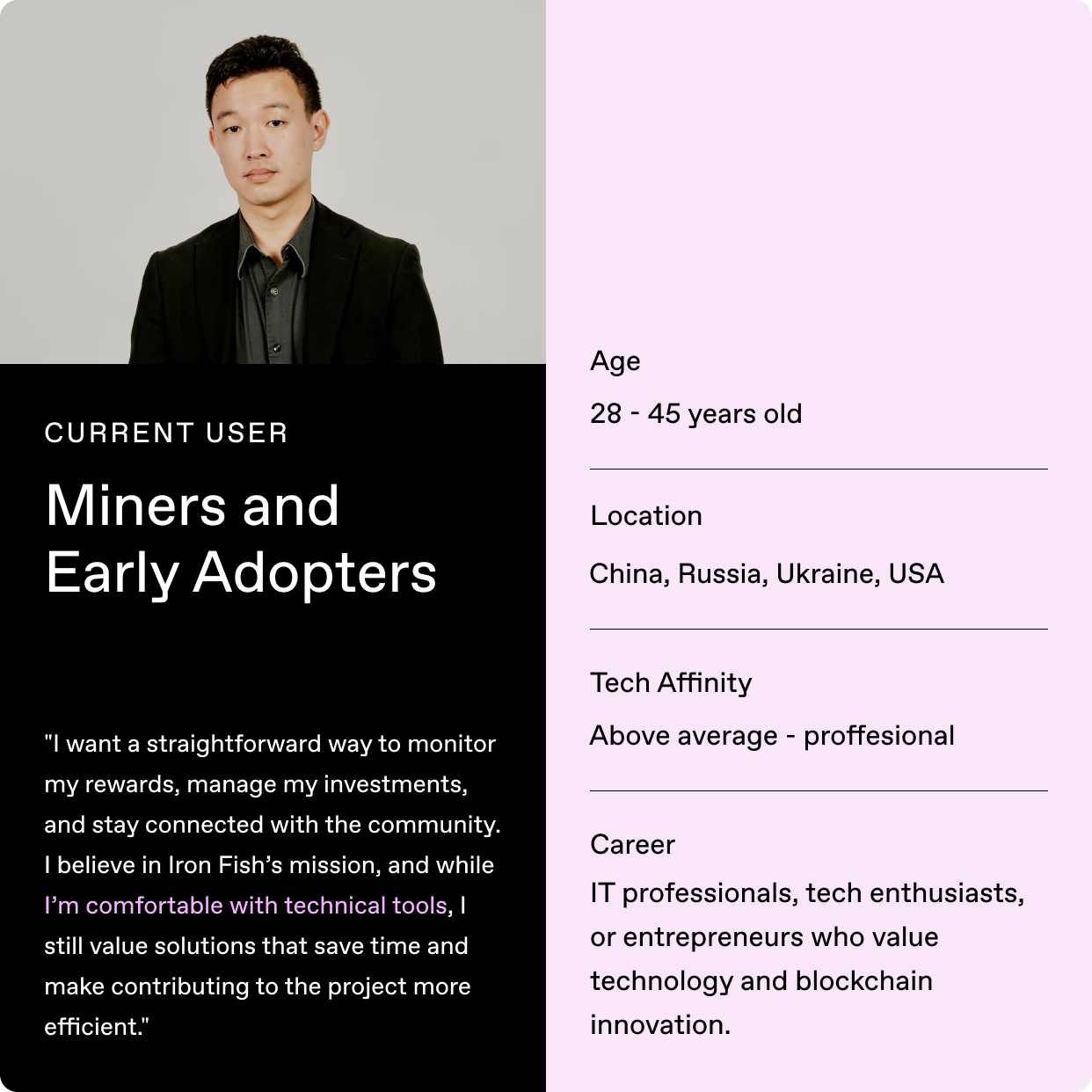
I started from scratch to build a mobile wallet that competes with industry leaders while adding robust privacy. Our two goals: (1) make privacy accessible and (2) bring the average crypto users—currently underserved by our products—into our network. Without this user, our network would struggle to gain traction.
THE SYNCING PROBLEM
Our challenge wasn’t just to create a mobile wallet that competes with industry leaders—it was to do so while preserving full encryption.
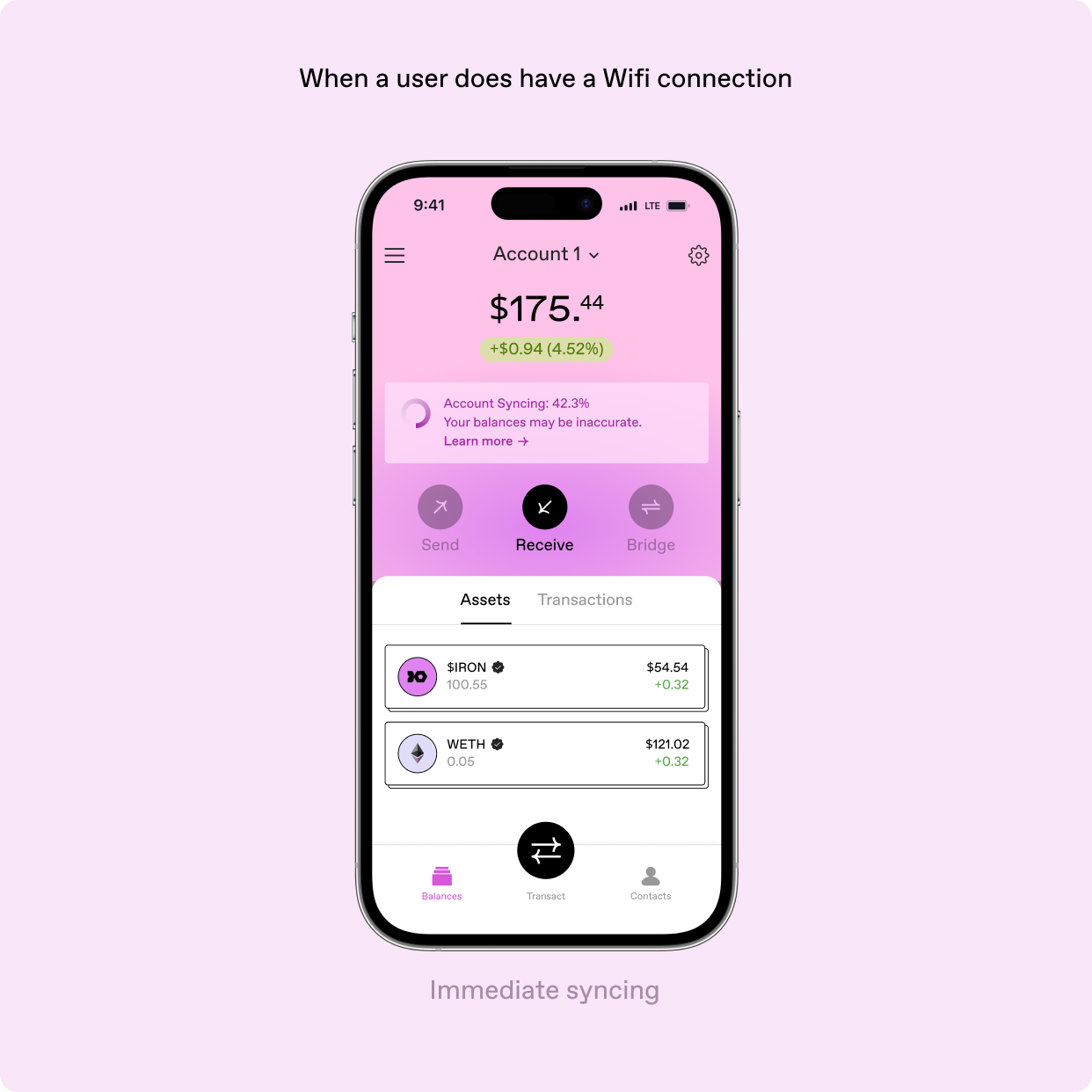
However, complete privacy requires running a node to encrypt user data, but syncing that node with the blockchain can take hours, placing a significant hurdle in the path to privacy.
WHAT OUR COMMUNITY HAD TO SAY
Our research confirmed this issue: syncing delays not only frustrate users but also discourage less technical audiences—crucial for Iron Fish’s broader adoption and growth—from fully embracing the network.
MOVING TOWARD A SOLUTION
I followed an iterative, three-step lean design process: Think, Make, Check. The emphasis on each step varied depending on the stage of the design lifecycle, allowing flexibility and focus as needed.
THE DISCOVERY
Spending more time in the problem space revealed that while average users value encryption, they don’t consider running their own nodes essential.
This insight presented an opportunity: technical users want full control, but everyday users simply want secure, encrypted data without the friction of node management.
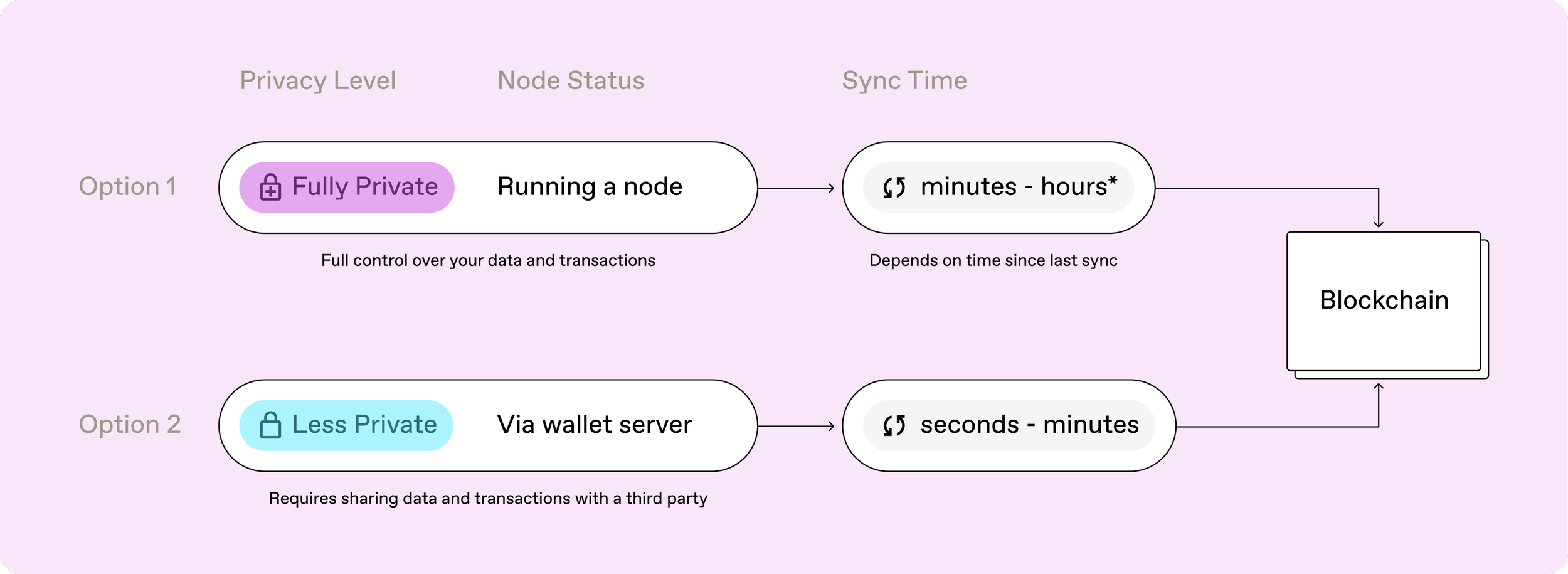
By advocating for a second level of privacy independent of running a personal node, I drove the idea that led to our engineering team repurposing the Wallet Server.
This proxy solution reduced sync times, maintained encryption standards, and made privacy more accessible to a broader, less technical audience.
THE EXECUTION
We decided to introduced two privacy levels in the mobile app:
Fully Private: Users run their own node for maximum privacy, maintaining full control of the encryption process.
Less Private: Users connect to the Wallet Server, which acts as a proxy, offering faster sync speeds and more accessible privacy.